All networked devices, including vehicles, are exposed to security threats and must be protected against many types of malware. Cyber Security Management Systems (CSMS) that are aligned with the current challenges can provide a useful organizational and process support for technical cyber security solutions for this purpose. We will discuss this and other topics in more detail in this article.
It wasn’t long ago that cyber security for vehicles was not a high priority for OEMs and suppliers. However, as the automotive industry continues to undergo a digital transformation driven by the proliferation of the ‘software defined vehicle’ and the development of new mobility concepts, cyber security has become a critical issue in the hardware and software value chain and is being taken more seriously than ever. New and future electronic architectures for automobiles based on fewer and larger control units, called domain controllers, will help simplify the current complex structures. However, due to increased connectivity with mobile devices, Wi-Fi networks, cloud platforms, smart cities and and other edge devices, much of the current complexity will remain. The following table summarizes examples of which systems within vehicle electronics need to be protected by cyber security:
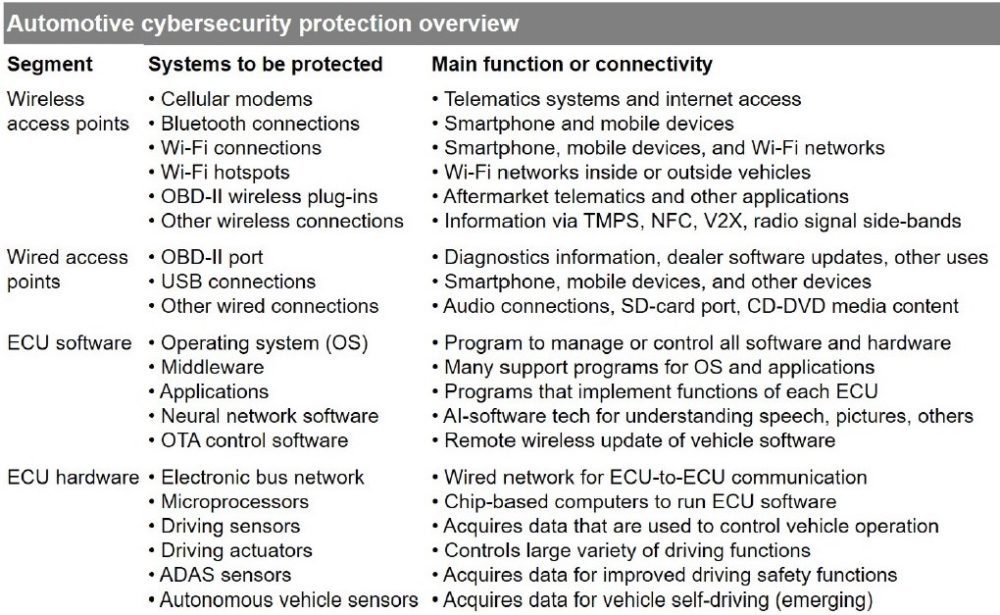
[Source: Automotive cyber security, 2021, Vivek Beriwat]
All in all, however, the entire end-to-end solution must be secured. In addition to the vehicle, this also includes the backend, the mobile devices and the respective telecommunications connections. Furthermore, cyber security protection must be maintained over the entire life cycle (approx. 30 years per vehicle series) of a manufacturer’s vehicle fleet. This results in requirements for the updateability of the software used. In addition, the entire hardware and software value chain must be protected against cyber security risks.
The importance of Cyber Security Management Systems
Supply chain attacks have been a security concern for many years, but planned organized attacks against b2b companies have been occurring in greater numbers since 2020. Perhaps due to the more robust security protections that b2c companies have put in place, attackers have shifted their focus to suppliers and have managed to cause significant impact in the form of system downtime, financial loss, and reputational damage, to name just a few of the damages.
The devastating consequences of software supply chain attacks were on full display as a result of the SolarWinds hack. The SolarWinds hack is considered one of the largest software supply chain attacks in recent years, especially considering the entities affected, which include government organizations and large corporations. The attack received a lot of media attention and led to policy initiatives around the world. More recently, in July 2021, the attack on Kaseya came to light and highlighted the need for more attention to software supply chain attacks affecting managed service providers. Unfortunately, these two examples are not isolated incidents; in fact, the number of software supply chain attacks has also steadily increased over the past year. This trend underscores the need for policymakers and the security community to develop and implement new protections to counter potential supply chain attacks in the future and mitigate their impact.
Cyber security in the automotive industry
Cyber security is a relatively new area for the automotive industry, but one that is steadily growing in importance due to the rapid proliferation of connected vehicles. In the future, all new vehicles will be connective. More connected vehicles mean higher risks, as connectivity brings new challenges that cannot be ignored.
Automotive cyber attacks lead to a variety of business risks within the automotive industry:
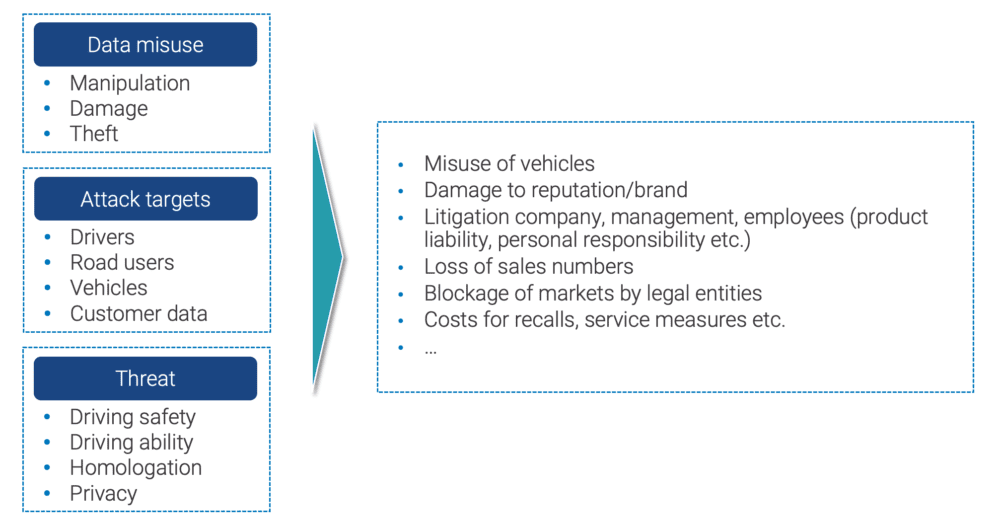
[Source: Magility GmbH, Management of cyber security threats and risks in the Automotive industry]
Connected cars therefore need cyber security protection. This includes embedded software programs to protect against cyber attacks on individual vehicles that are available at the time of sale, but also cloud-based cyber protection services for the vehicle fleet that can be specifically activated during use. These trends have led to a growing need for software and hardware cyber security products and cloud-centric services which have become a critical core product and value chain issue for OEMs and their suppliers.
Legislators have therefore reacted and, from 2022, car manufacturers will have to prove for type approval that they can protect their vehicles and fleets against cyber attacks and that they are capable of managing cyber security in terms of processes and organization. Currently, there are already national and international activities for the standardization of Cyber Security Management Systems and their auditing. Those who have to deal with these challenges must also deal with various regulations and standards.
As an example, the formal regulatory cycles for UNECE are shown below:
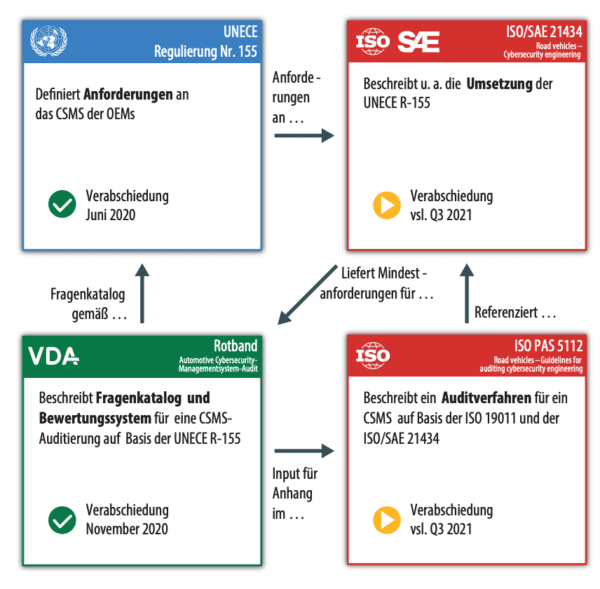
[Source: Quality Institute/VDA, UNECE standards and rules]
In order to make all these comprehensive regulations manageable, Magility recommends tailor-made integration of the same into the company-specific development, production, sales and after sales systems.
Magility’s Cyber Security Management System (CSMS)
Automotive Cyber Security is therefore emerging as a new interdisciplinary enterprise system function. Magility is starting precisely here and is now focusing all the more strongly on supporting automotive companies and their suppliers in dealing with new threats. One of the tools we recommend for this purpose is a CSMS tool for raising awareness and combating cyber risks on a sustained basis:

[Source: Magility GmbH, Management of cyber security threats and risks in the automotive industry, Automotive Cyber Security Management System (CSMS)]
Cyber Security Requirements of the Top Management – Goals and code of conduct for cyber security
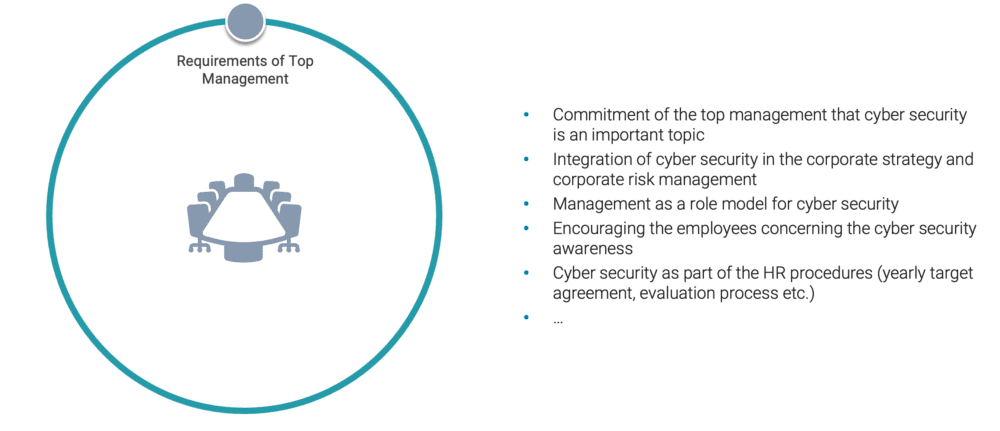
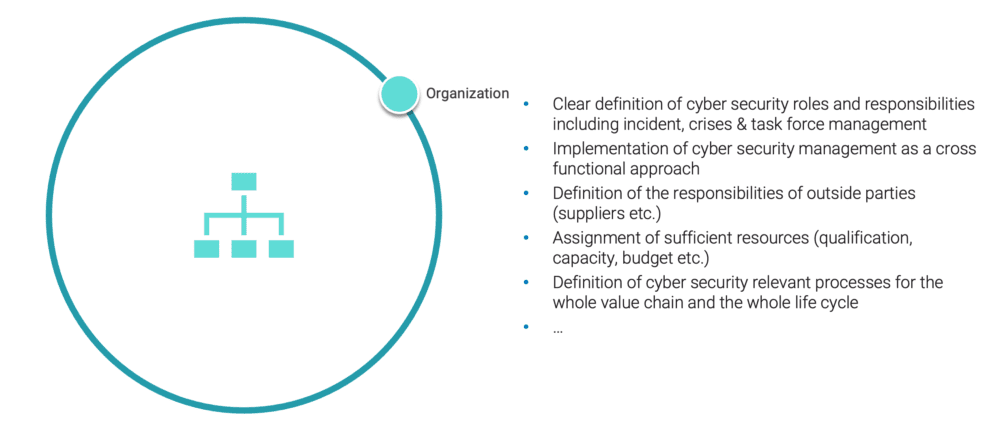
Cyber Security Organization – Definition of roles and responsibilities
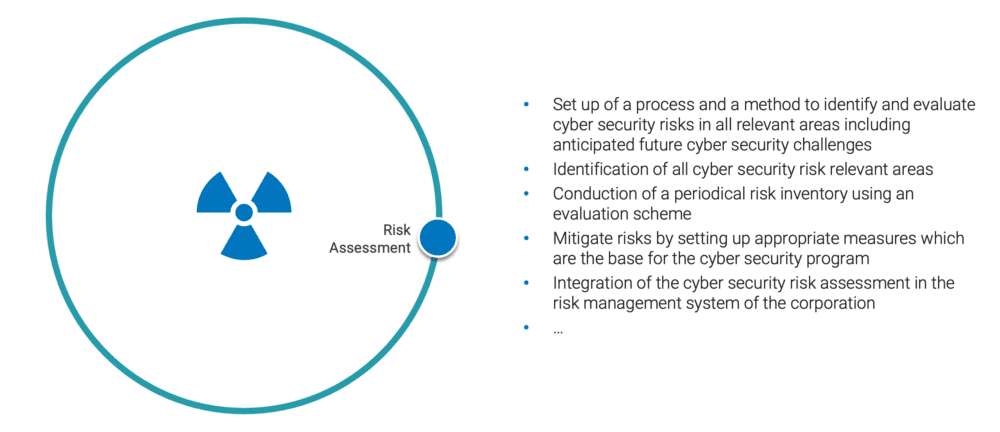
Cyber Security Risk Assessment – Identification and evaluation of cyber risks
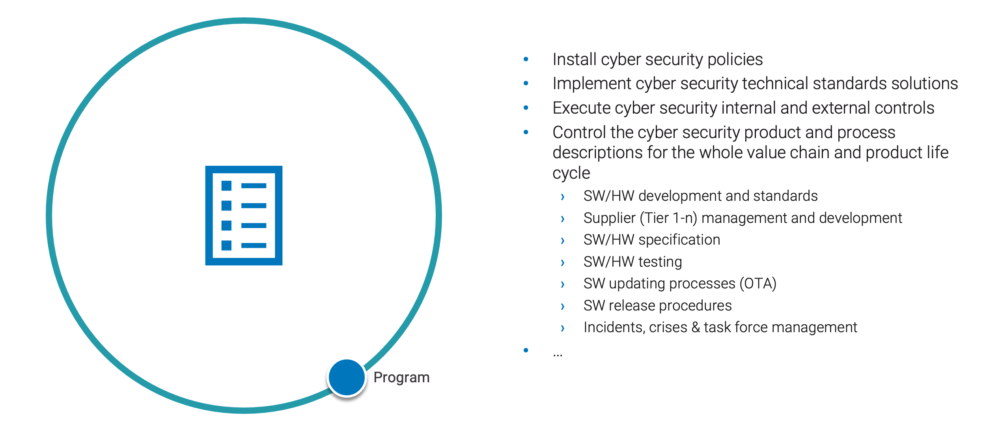
Cyber Security Program – Structure, execution and control of cyber security policies
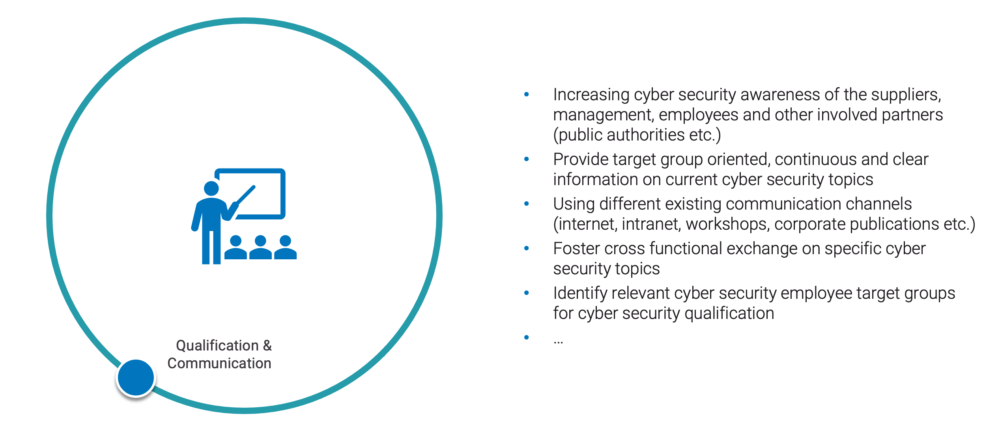
Cyber Security Qualification and Communication – Increasing cyber security awareness
Cyber Security Implementation – Sustainable protection of the company and corporate customers
Cyber Security Effectiveness Monitoring – Assessing the effectiveness of cyber security measures
Cyber Security Audit – Definition of roles and responsibilities for CSMS effectiveness monitoring
Magility recommends that companies implement the CSMS regulatory cycle outlined above in order to respond agilely as an organization to new potential threats, to increase awareness of cyber security among all employees, and to ensure a continuous cyber security improvement process for new vehicles and the existing fleet.
Magility is strongly focused on further expanding the cyber security capabilities and CSMS competencies to meet the threats of the future and present. For further information or a personal consultation, please contact our Managing Director Dr. Michael Müller (michael.mueller@magility.com) as well as our cyber security consultant Hanna Kahindi (hanna.kahindi@magility.com).
Follow us on LinkedIn for new articles and other news about cyber security, or contact us directly via our contact form if you have any questions. We are looking forward to it!



